Whitelists and Remote Whitelists in FNM Manager
Introduction
FastNetMon includes two types of whitelists for managing network exceptions that should not be blocked during DDoS attack detection:
-
Whitelist: Local networks that should not be sent to blackhole.
-
Remote Whitelist: External networks that should also be excluded from blocking.
These functionalities are easily managed through the "Block Manager" module in FNM Manager, offering granular control over networks that need differentiated protection.
Configuring Whitelists
Local Whitelist
The local whitelist is useful to prevent traffic from internal networks from being blocked during mitigation. This ensures that critical services within the infrastructure continue to function without interruptions.
Example of configuration in FastNetMon:
sudo fcli set main networks_whitelist 192.168.0.0/24
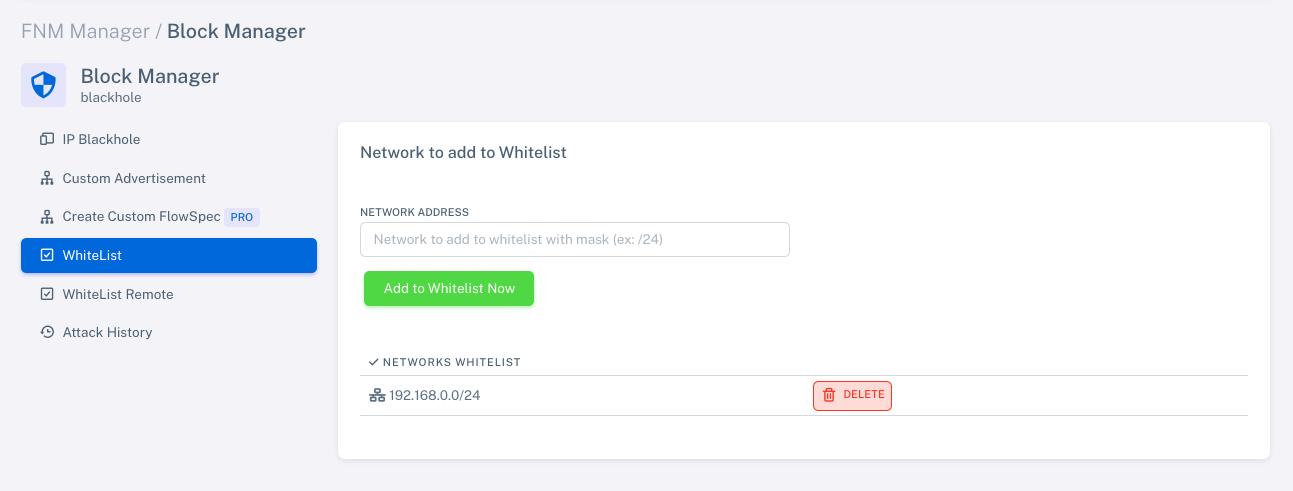
In FNM Manager, you can add local networks through the section:
-
Block Manager > Whitelist.
-
Enter the network address with its mask (e.g., /24) and click "Add to Whitelist Now".
Remote Whitelist
The remote whitelist allows excluding external networks from blocking. This is useful to prevent interruptions in traffic to and from specific partners, providers, or key clients.
Example of configuration in FastNetMon:
sudo fcli set main networks_whitelist_remote 8.8.8.8/32
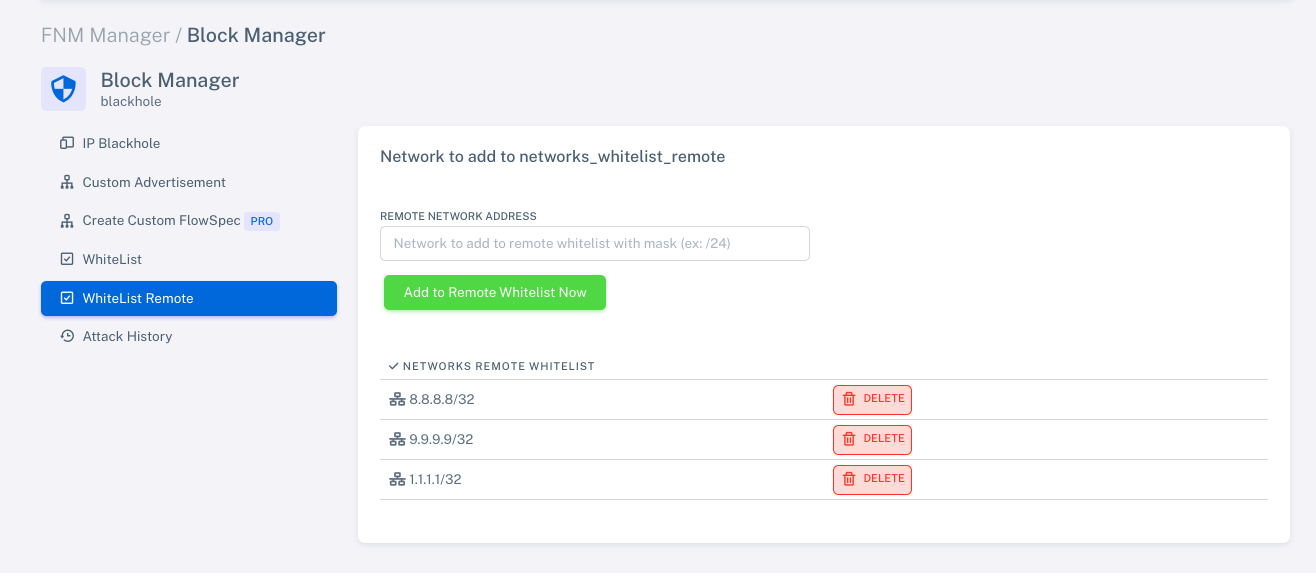
In FNM Manager, you can add remote networks through the section:
-
Block Manager > Remote Whitelist.
-
Enter the external IP or network address with its mask and click "Add to Remote Whitelist Now".
Reasons to Create Exceptions
-
Critical Local Services: Avoid blocking networks that host important internal services, such as internal DNS servers, databases, or email systems.
-
Partner and Provider Networks: Ensure uninterrupted connections with strategic partners or key providers during attack mitigation.
-
Priority Clients: Exclude traffic from important clients or critical networks to maintain their uninterrupted experience.
-
Essential Public Services: Prevent blocking of services like trusted public DNS servers (e.g., Google’s 8.8.8.8).
Benefits of Using Whitelists
-
Customized Mitigation: Allows excluding specific networks from blocking without compromising overall security.
-
Service Continuity: Ensures that critical services remain operational during a DDoS attack.
-
Improved Customer Relationships: Ensures that connections with key external networks are not affected.