How To: Implement a Scrubbing System with FastNetMon and FNM Manager PRO
Objective
Implement an automated scrubbing system using FastNetMon and FNM Manager PRO so that, upon detecting an attack, the affected network is redirected to a traffic cleaning provider (e.g., PATH.net, Voxility, etc) using BGP community-based routing policies.
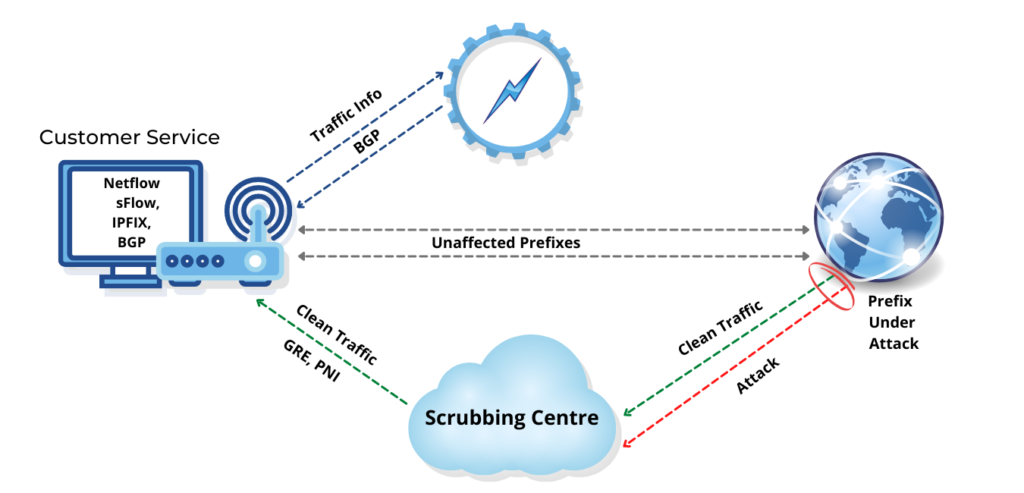
Scenario
We have:
-
A router that maintains a BGP session with our main Internet carrier.
-
An additional BGP session with the scrubbing provider (PATH.net).
-
A GRE tunnel established with PATH.net.
-
FastNetMon & FNM Manager connected to the same BGP router, with control over BGP announcements.
Step 1: Configure FNM Manager PRO to Delegate BGP
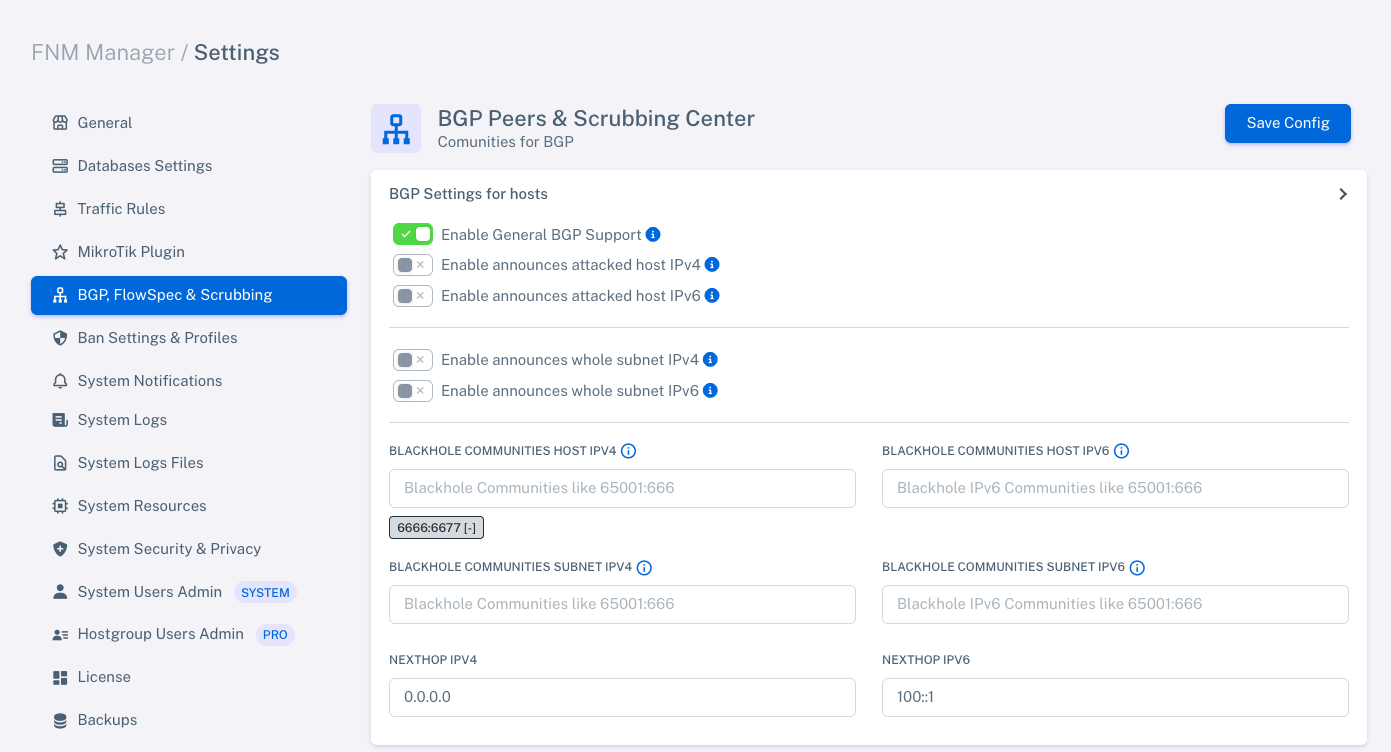
Go to Settings > BGP Peers & Scrubbing Center and follow these steps:
-
Enable "General BGP Support".
-
Disable all announcement options (announces attacked host, whole subnet, etc).
This setup allows the FastNetMon BGP daemon to connect to peers without making any announcements. All announcements are controlled exclusively by FNM Manager PRO.
%2018.32.13.png)
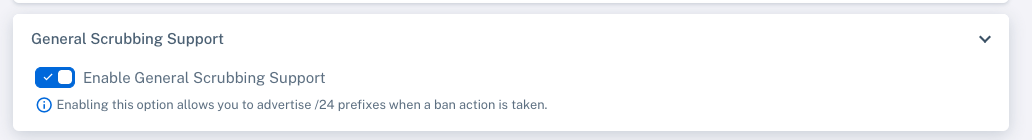
Step 2: Enable Scrubbing Support
From the same section, enable:
- "General Scrubbing Support"
This allows the system to advertise /24 prefixes during a ban action.
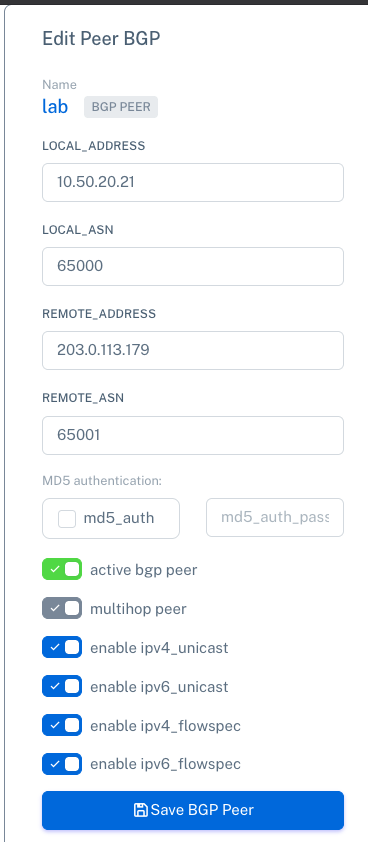
Step 3: Create BGP Peer in FNM Manager PRO
Go to the "BGP Peers" section and add the peer that connects to your BGP router. For example:
-
Local ASN: 65000
-
Local Address: 10.50.20.21
-
Remote ASN: 65001
-
Remote Address: 203.0.113.179
This peer will handle the redistribution of prefixes based on the routing policies. Note that different ASNs are used on both ends to ensure this is treated as an eBGP session. If both ends used the same ASN, it would be considered an iBGP session.
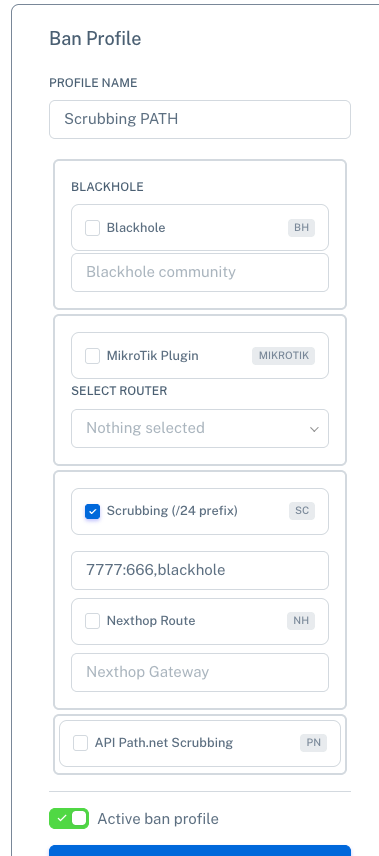
Step 4: Create Ban Profile with Scrubbing
Go to Settings > Ban Settings & Profiles:
-
Create a new profile or edit the existing one.
-
Enable "Scrubbing (/24 prefix)".
-
Enter the BGP community to be used (e.g.,
7777:666). -
Set the profile as active.

Step 5: Apply Scrubbing to Hostgroup
From the Customers section, you can configure which hostgroups will use scrubbing:
-
Enter the desired hostgroup / customer or the global profile (
Customers > global). -
Click the "Settings" or "Configure" button within the hostgroup to open its specific configuration.
-
In step 3 of the assistant ("Ban Profile"), select the scrubbing profile created.
If scrubbing is to be applied to all groups, it is recommended to edit the "default" profile. If only specific customers require scrubbing, different profiles can be assigned per group.
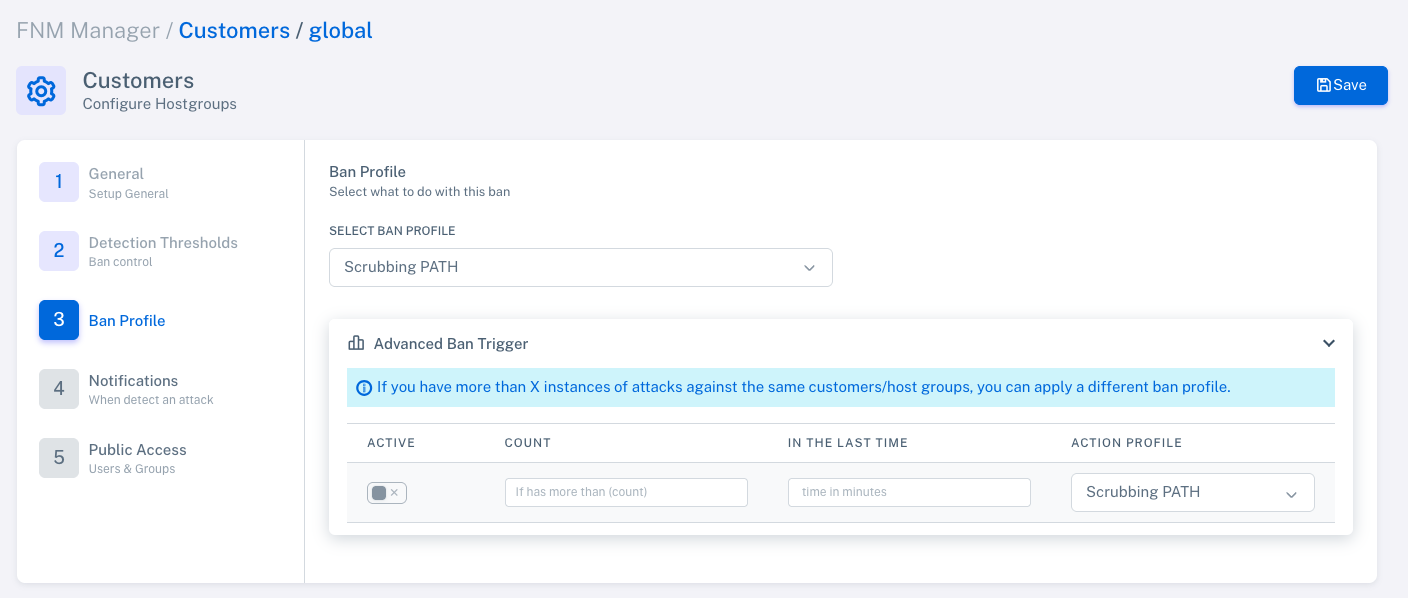
Advanced Conditional Activation
You can enable the "Advanced Ban Trigger" option to apply a secondary profile if multiple attacks are detected within a short time frame. This allows escalation of mitigation based on the attack behavior.
Step 6: BGP Router Configuration for Scrubbing
The router must apply routing policies so that when a specific community (e.g., 7777:666) is detected, the prefix is withdrawn from the carrier and announced exclusively to PATH.net.
BGP Filters in MikroTik RouterOS
/routing filter
add action=accept bgp-communities=7777:666 chain=fnm_in prefix-length=24
add action=discard bgp-communities=7777:666 chain=to_carrier_out prefix-length=24
add action=accept bgp-communities=7777:666 chain=to_path_net_out prefix-length=24
BGP Peer Configuration
/routing bgp instance
set default as=65001
/routing bgp peer
add address-families=ip,ipv6 in-filter=fnm_in multihop=no \
name=to_FASTNETMON out-filter="fnm_out" remote-address=10.50.20.21 remote-as=65000 \
update-source=203.0.113.179
add in-filter=to_carrier_in multihop=no name=to_CARRIER \
out-filter=to_carrier_out remote-address=13.20.20.1 remote-as=65333
add in-filter=to_path_in multihop=no name=to_PATH \
out-filter=to_path_net_out remote-address=200.200.200.200 remote-as=396998
With this configuration, prefixes marked with the defined community will be redirected to PATH.net, who will scrub the traffic and return it through the established GRE tunnel.